Views: 382 Author: Site Editor Publish Time: 2021-03-17 Origin: Site








Stream voice and data via an 'infrastructureless' network
Infrastructure-based radio communication systems such as DMR, TETRA, P25 etc, which rely on cellular, fiber cable, IP connectivity or WiFi technology to deliver voice and data to the users. IFLY Wireless Mesh Networking (also called MANET, or Mobile Ad hoc Networking) communciation radio systems is the system that removing those infrastructure and adding mobility without any affecting the user’s high quality of service.
A MANET critical communication radio system is a group of mobile (or temporarily stationary) devices which provide stream voice and data between handset radios utilizing the portable base station as relays to avoid the need for infrastructure.
There are many techniques which are employed in order to provide robust MANET capability, including the following:
In an adhoc network, mobile nodes communicate with each other through multi-hop wireless links. The entire network doesnt need any fixed infrastructure, such as cellular coverage, fiber cable etc. Every node in the network can act as a router to forward data packets to other nodes. Developing a dynamic routing protocol that can effectively find routes between nodes has become the key to adhoc network design.
The adhoc routing protocol must be able to detect dynamic changes in the network topology. Because the adhoc network requires multi-hop communication. Therefore, the routing protocol must ensure that the links in the path have strong connectivity. The nodes in the adhoc network must know its surrounding environment and the nodes that can directly communicate with it. There are two main ways to provide network connection in adhoc network: flat routing network structure and hierarchical routing network structure (Figure 1). In the flat routing network structure, all nodes are equal, and the routing of packets is based on peer-to-peer connections. However, in the hierarchical routing structure, there must be at least one node in the lower layer as a gateway to connect with the upper layer.
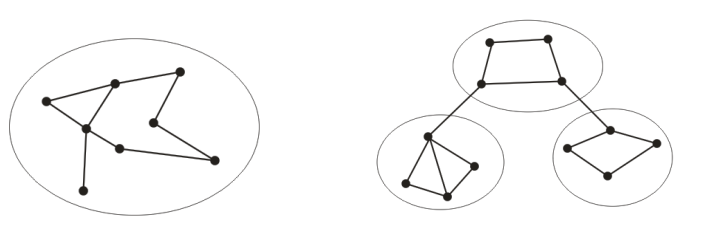
Figure 1: Flat Structure and Hierarchical Structure
Because each mobile device can change its location at any time, the network topology changes frequently. In this way, the ad hoc routing protocol must dynamically update the link state and reconfigure itself in order to maintain strong connectivity between the nodes. If a centrally controlled routing algorithm is used, it will consume too much time and energy in order to transmit the change of node link status to all nodes, which is obviously not suitable. Therefore, a fully distributed routing algorithm must be adopted.
Compared with static nodes in wired networks, ad hoc networks require a highly adaptive routing mechanism to handle rapid topology changes. Traditional routing protocols, such as distance vector and link state algorithms, require a large amount of routing information to be exchanged between designated routers, so they cannot work effectively in ad hoc networks. Therefore, a new routing algorithm is proposed for the characteristics of ad hoc networks. In general, these routing algorithms can be divided into three types: table-driven algorithms, demand-driven algorithms, and mixed algorithms of table-driven and demand-driven algorithms.
The table-driven routing protocol uses periodic routing packet broadcasts to exchange routing information. Each node maintains routes to all nodes in the entire network. The demand-driven routing protocol performs the routing discovery process on demand according to the needs of the sending node. The network topology and routing table content are also established on demand, so its content may only be part of the entire network topology information.
The current security strategy is a password-based authentication protocol. It is different from traditional password authentication. The generation of its key and password is determined by multiple devices, not by one device. It also provides a perfect password update mechanism: the "resurrected duck" security model. It mainly addresses the possible insecurity issues between the sensor and the controller in the sensor network, and proposes that the sensor is only controlled by its owner before "death". Asynchronous distributed key management, which proposes that the key management service is managed by multiple nodes (a set) instead of a single node.
The wireless ad hoc network is a multi-hop network. The gateway router can realize the function of interconnecting several ad hoc networks and the nodes in the network can access the Internet. This form can provide collaborative communication capabilities to work groups located different locations. The wireless ad hoc network is interconnected with the Internet and WAN. From the outside, it can be considered that the ad hoc network is an IP subnet. The transmission of some packets in the network is completed by the routing protocol in the network (the packet may have to go through multiple hops to reach the destination), and when the packet enters or leaves the subnet, the standard IP routing mechanism is used. This requires the gateway node to be able to run multiple routing protocols.


